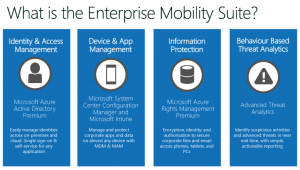
MICROSOFT EMS OVERVIEW
Microsoft Enterprise Mobility + Security Suite (EMS) is an add on to the Enterprise E3 and E5 licences that bundles some other services into one price to focus on additional security. This blog post only touches on the key aspects of EMS which we will cover in more detail in other blog entries.
There are four key parts to EMS:
- Azure Active Directory Premium
- Microsoft Intune
- Azure Information Protection
- Microsoft Advanced Threat Analytics
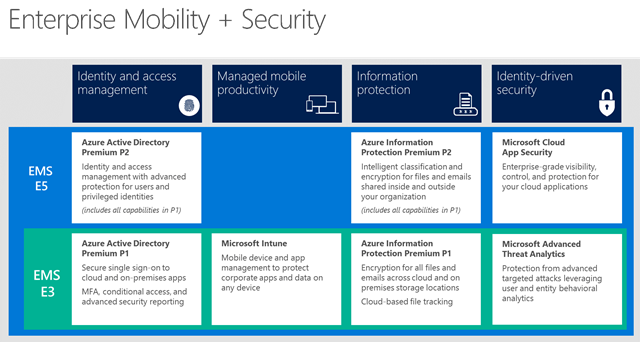
The E3 version contains the basic version of the four products included in EMS as set out below while E5 has some extra elements:
- The P2 Version of Azure Active Directory with new Identity Protection and Privileged Identity Management capabilities. These new functions help protect against identity theft, and provide additional usage data on admin actions.
- The P2 Version of Azure Information Protection. It adds automatic classification to your feature list. This means documents can be automatically encrypted, rather than the “manual” encryption method in P1.
- Risk-based conditional access. This protect apps and critical data in real time using machine learning and the Microsoft Intelligent Security Graph to block access when risk is detected.
- Microsoft’s new Cloud App Security that can help you discover the cloud apps in use in your network, and control access to those apps. For example, it will inform you of which 3rd party services an employee may be using without authorization.
E5 EMS is double the price of E3 EMS as of the end of 2017. If you can answer yes to any of the questions below then you need E5.
- Do you want Azure Active Directory to provide you with extra data regarding potential identity theft in your organization?
- Do you want Azure Active Directory to provide you with extra data regarding the actions that administrators take in your account?
- Do you want Azure Information Protection to automatically encrypt your files? Otherwise, your protection settings can only be added manually.
- Do you want control over the external cloud applications that your employees use?
Azure Active Directory Premium
Azure AD is a huge product and is at the heart of many Office 365 products. It has many features and this section highlights a few. With Enterprise O365 licences you get the basic version that includes:
- Single sign on
- Two factor authentication
- Basic usage reporting
- Company branding
With Azure AD P1 you get basic plus:
- Microsoft Identity Manager - needs a Windows server instance
- Cloud app discovery
- Conditional access based on group and location
- Conditional access based on device state
With Azure AD P2 you get P1 plus:
- Identity Protection / Conditional access based on sign-in or user risk
- Privileged Identity Management
- Windows 10 MDM auto-enrolment and Self-service Bitlocker recovery
Microsoft Intune
Microsoft Intune is a cloud service that provides device control for Windows, Windows Mobile, iOS, Android, and Mac OS X. It is administered inside the Azure portal and can help towards GDPR. It includes:
- Mobile Device Management (MDM) that allows corporate IT to control device management, inventory, app deployment, provisioning, and retirement. Control incudes the likes of password ageing, VPN and WIFI connectivity, and location based usage.
- Mobile Application Management (MAM) that allows the setting of restriction policies at the app level for use with or without MDM device enrollment. Intune’s MAM capabilities enable IT to help protect corporate data with the policies that restrict data leakage such as “Cut/Copy/Paste/Save As”, provide encryption at rest, enforce application access and compliance, and remove corporate data at the application level.
- Conditional access to corporate data with its conditional access capabilities which ensure that only managed and compliant devices are able to access corporate email and files.
- Management of Office 365 and Office mobile app Intune has unique capabilities to manage Office mobile apps including app-level authentication, copy/paste control, save as control, and enforce conditional access policies to Exchange Online, Exchange on-premises, SharePoint Online, and Skype for Business. Intune also enables multi-identity scenarios, which allows users use both personal and company accounts within the same Office mobile app.
- PC Management for computers running supported operating systems using the Intune agent or via MDM. This works with System Center Configuration Manager to support more advanced PC and server management scenarios.
Azure Information Protection
Azure Information Protection (AIP) helps an organization to classify, label, and protect its documents and emails. This can be done automatically by administrators who define rules and conditions, manually by users, or a combination where users are given recommendations. AIP is in addition to the Data Loss prevention (DLP) that comes with Enterprise Licences.
The protection technology uses Azure Rights Management (often abbreviated to Azure RMS) for encryption, identity, and authorization policies. Similarly to the labels that are applied, protection that is applied by using Rights Management stays with the documents and emails, independently of the location—inside or outside your organization, networks, file servers, and applications. This information protection solution keeps you in control of your data, even when it is shared with other people.
Microsoft Advanced Threat Analytics
Microsoft Advanced Threat Analytics (ATA) provides a solution to help protect your organization from advanced attacks. It uses a number of methods to identify and provide alerting to attacks in your environment before they actually cause any damage. Think of it like the technology banks use to watch your normal usage patterns and alert you for something out of the ordinary.
Rather than constantly reporting and providing endless reams of information, ATA can identify anomalies quickly, helping you to focus on alerts that could indicate a problem. The key methods used are:
- Behavioural Analytics learn the normal patterns of users and the devices they use. Patterns outside the normal will be flagged such as using different devices or working different/longer hours. This is enabled through machine learning and data from Active Directory.
- Detection for known malicious attacks and security issues.
Related
Full E5 introduction and video
Simple EMS overview video
Mac device compliance for EMS Conditional Access using Microsoft Intune integrated with Jamf Pro