Increasing Windows RDP security without a CA
For windows 7 and above the built in Remote Desktop access for support uses a self-signed certificate that makes use of the now deprecated SHA1. If you delete the certificate and reboot, or start/stop the RDP service, the self-signed certificate gets auto recreated with the same SHA1 and so far I have not found a way to increase the encryption standard for the auto creation.
You can of course use a Certificate Authority (CA) server but this only usually exists in large organisations. If you do have a CA then this article is useful.
Set out below is a process to use a stronger certificate.
- Using a windows machine with PowerShell 3 or greater user the script New-SelfSignedCertificate to create a new certificate. Make sure to:
- # Set number of bits to at least 2048
- # Use at least SHA256
- # Set expiry no longer than 3 years
- # Make a note of the SHA thumbprint
- There are other ways using the command line using MakeCert but this has been deprecated in favour of the PowerShell script.
- Using MMC open the certificate management for the “Computer account” on the machine you want to increase the RDP for.
- Import the new certificate in the personal store.
- Set the certificate to have NETWORK SERVICE -> READ security by right clicking on the certificate and selecting All Tasks -> Manage private keys.
- Using the registry editor open HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp and add a new binary key called SSLCertificateSHA1Hash with the thumbprint of the new certificate.
- Reboot the machine
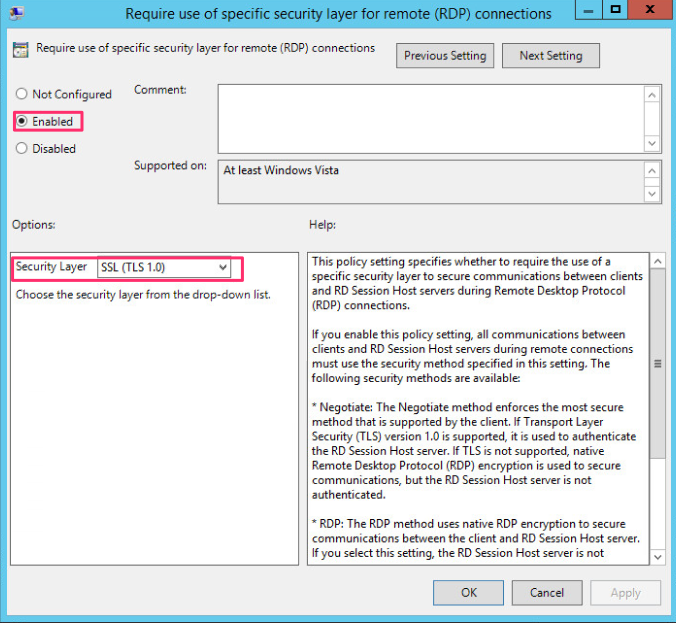
It is also advisable to use a policy to set the RDP security level as shown. At present this only allows up to TLS1.0.
Now in addition to the above I strongly recommend you look at the encryption and cyphers configuration. You are best to use the IISCrypto.exe tool which helps with this. Also make sure you have all the KB patches loaded to support this and the related registry keys.
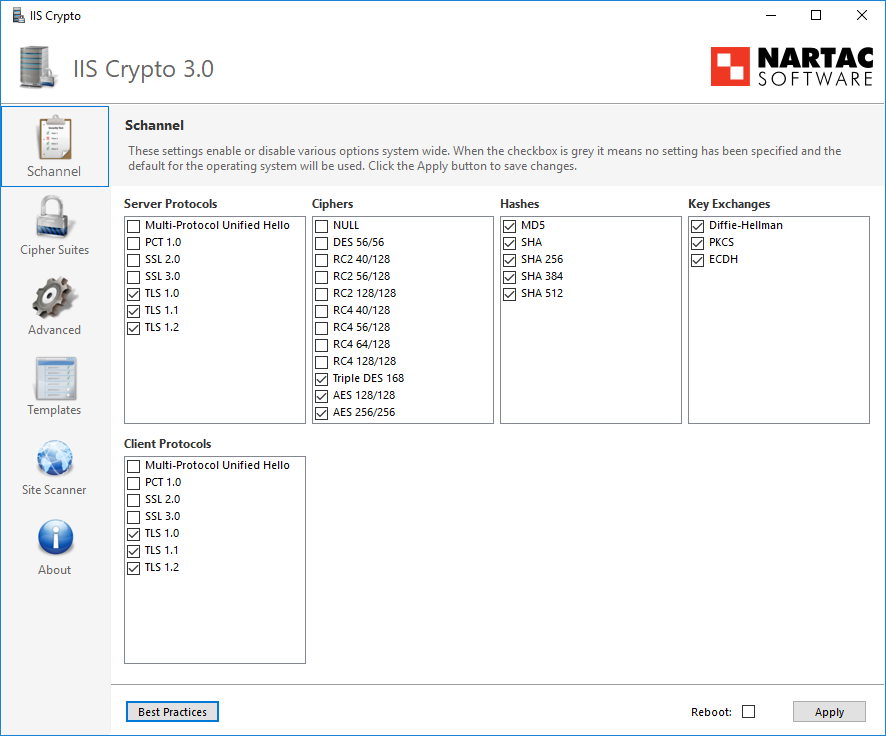
- Enable TLS 1.0, 1, and 1.2 in the HKLM for Client and Server. If SSL 3 is not there set it up but disable SSL2 and SSL3 for Client and server. NOTE that this applies to all circuits on the computer including browsers.
- Restrict the Hashes used.
- Restrict the cipher suites . For more on cyphers see the OWASP article.