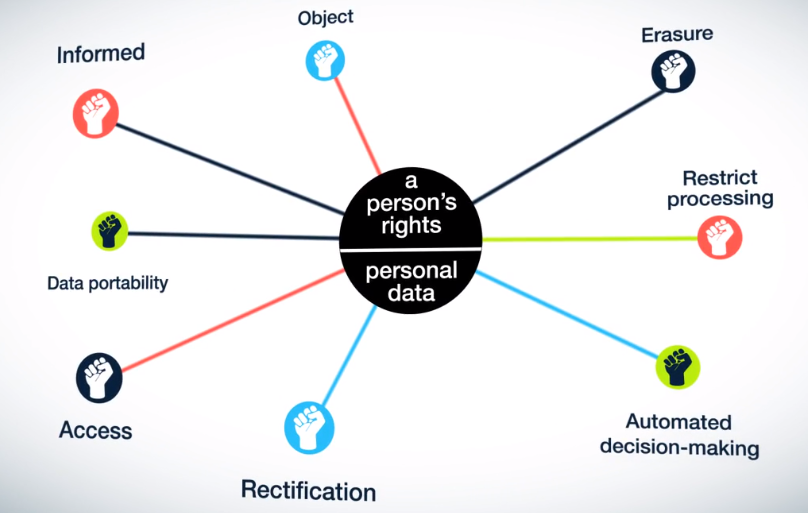
GDPR Musings
This article has been put together to set out some areas on GDPR for SME details I have gleaned from various sources since October 2017.
None of the points in this article are to be taken as fully correct and in all cases when complying with GDPR you should consult your local Information Officers, Data Protection Officer, and legal sources.
All parts of the GDPR regulation are not necessarily included so please use the EU source documents.
The Privacy and Electronic Communications Regulations (PECR) sit alongside the Data Protection Act and the GDPR. They give people specific privacy rights in relation to electronic communications.
There are specific rules on:
• Marketing calls, emails, texts and faxes
• Cookies (and similar technologies)
• Keeping communications services secure
• Customer privacy as regards traffic and location data, itemised billing, line identification, and directory listings
The GDPR does not replace PECR, although it changes the underlying definition of consent. Existing PECR rules continue to apply, but using the new GDPR standard of consent.
This means that if you send electronic marketing or use cookies or similar technologies, from 25 May 2018 you must comply with both PECR and the GDPR.
- Use checklists such as here and here
- Find all your data subject touch points (phone / service desk/ messages / website /paper/ marketing interactions) and get the users to document the process and the data flow
- Document who has access to data, where it was from, how long it has to be kept and why
- Perform DPIA on the processing
- Sort out your privacy notice/policy
- Check consent capture and recording
- Setup a Data Subject Access Request (DSAR) handling process
- Sort out a data breach reporting process
- Review/create audit and housekeeping processes
- Check access controls for paper/electronic access from network shares and drawers/file cabinets/rooms
- Have an IT security, access and data retention policy
- Make sure all procurement and relationship managers identify supplier/3rd party interactions that need critical controls in place or contracts changing
- Create procedure to action requests from subject for data to be changed, completed, corrected or deleted
- Create procedure to check that data is up-to-date
- Make sure to review, document, and monitor physical security of premises, such as good quality locks, alarms, security personnel, entry controls and CCTV, at whatever level is necessary
- A company or entity which processes personal data as part of the activities of one of its branches established in the EU, regardless of where the data is processed
- A company established outside the EU offering goods/services (paid or for free) or monitoring the behaviour of individuals in the EU.
Requesting consent
- Consent requests should be kept separate from general terms and conditions and should be in clear, easy to understand language
- Avoid confusing or technical language and use consistent language across consent options
- In order to make your consent requests as specific and informed include the name of your organisation and any third parties who will be relying on the consent or data, why you want the data and what you are going to do with the data
- You should also make clear to customers that they can withdraw consent at any time and how to do this
Recording consent
Once consent is obtained, it should be recorded in a manner which allows you to keep a record of how and when consent was given by an individual. In order to keep good records on consent, you should be able to show who consented, when they consented, the information they were provided with prior to consent and how they consented. The information, for completeness, should also include whether they have since withdrawn that consent. How you comply with this obligation will differ from organisation to organisation; however, it may mean, for example speaking to your software developer to see if your current systems can assist you here or whether they can help your management of this obligation.
Managing consent
Consent is part of your ongoing relationship with individuals and should therefore be managed appropriately:
- It is good practice to provide individuals with preference tools where they can easily access and manage their consent and change their preferences if needed.
- If anything about the original consent changes, in any way e.g. the nature of the data you are processing or, for example, you now want to process the data for a different or additional purpose, then you will need to get fresh consent from the individual – that’s only fair.
- If there have been no changes in the data processing, it is good practice to refresh consent on a regular basis. The ICO recommends refreshing consent every 2 years – but you will need to think about what is appropriate to your business and the type of data you collect and use – and even the individuals from whom you collect the data.
- The GDPR gives individuals the right to withdraw consent at any time. You must provide a mechanism for the individual to withdraw at any time, on their own volition. You must make it as easy to withdraw consent as it was to consent originally. You should be able to manage withdrawals of consent and ensure that data processing is stopped as soon as possible after the withdrawal is made.
An integral part of GDPR compliance is producing appropriate documentation, including a privacy notice. A privacy notice is a public statement that describes how your organisation collects, uses, retains and discloses its personal information.
Articles 12, 13 and 14 of the GDPR outline the requirements on giving privacy information to data subjects. The information provided must be:
- Concise, transparent, intelligible and easily accessible;
- Written in clear and plain language, particularly if addressed to a child; and
- Free of charge.
Any privacy notice or fair processing notice on printed forms, or which pop up on screen, before people fill in their personal details must explain who you are, what the data is going to be used for and who else will have access to it. It should also tell the person that they can remove their data whenever they wish.
If the details are taken over the phone you need to tell people this information.
To make processing ‘fair’, in most cases this means that the person must give their consent for their data to be used. Silence or inactivity is NOT consent - for example, agreement can’t be assumed by saying ‘tick here if you don’t want to receive information’; instead, it must be a clear ‘yes’ of agreement. It must be their deliberate choice to share their personal data. And they must know what they’re agreeing to.
Remember, children are considered to be vulnerable people under the GDPR, so extra care needs to be taken if you’re processing their data. You’ll need to get consent from their parents or guardians before you can do anything.
You must always keep a record of consent, because you must be able to show that it was given.
It’s really important that you don’t deceive or mislead someone about what their personal data is going to be used for. This would be ‘unfair’ use of their data.
To respond to a Data Subject Access Request (DSAR) remember:
• To fulfil the DSAR the person must provide enough data to be able to find them in your records
• Check to see if you already have an active request or already fulfilled one for the person
• Check they are who they say the are
• Retrieve all personal data held in emails and within ad-hoc files
• Redact files to ensure that where the data you want is mixed in with data about other people the other data is not available.
• Detail when and where the data you have came from.
• Decide how you will provide them with a machine readable, structured, electronic copy of all their data – possibly JSON or XML
DSAR can come in many ways:
• Email to any person in company
• Post
• Twitter
• Facebook
• A verbal request
When responding to a DSAR put the reply on a file share/SFTP and encrypted with a very short shelf life - otherwise you create another instance/"point" of personal data.
The UK ICO says “"If an individual makes a request electronically, you should provide the information in a commonly used electronic format, unless the individual requests otherwise."
- Recording calls
ICO says that calls can be recorded but general option is that apart from justifiable legitimate interest then any recording could potentially contain personal data, then the GDPR kicks in and then you need explicit consent. legitimate interest is hard to cover but is likely to include legal, contract, police, health but it is debatable if “for training purposes” is valid without consent.
- Signatures
Whether digital or hand written, are personal data. Signature is not only personal data but also sensitive information of an individual. If the data subject is identifiable, the risk of this information being misused increases significantly.
- Images
Some have argued that images of person can also be included as the image could be indicative of political opinions (e.g., wearing a party favour), sexual life (e.g., engaged in some sexual activity), health condition (e.g., pregnant, wearing a straight-jacket, showing disfigurement from disease), and commission of an offence (e.g., crime scene imagery). The commission has given guidance of a sort in Recital 51 . In addition they cover image for children .
- Know where the stuff is and how each of your systems treats the data. Which almost certainly means the need to understand data structures so that, say, like for like translation of scope, value and meaning,, as a matter of master data definition, can be reliably defined. Because until you do that...
- You can't identify the people who actually control the data in each of your silos such that a process can be defined to co-ordinate across multiple data forms. And when you have done that...
- You can then sequence the delete event such that referential integrity can be proved to be reliable. Which is important because...
- It may well be that an end to end deletion may not be possible because of compliance conflict associated with the need to comply with more than one set of rules and regulations at one and thee same time, because...
- RTBF means being able to understand every relationship between "person as thing" and organisation in that person can have more than one interaction at one and the same time. For example, person can be both customer and employee...
- And you need to understand that kind of thing because it may be the case that you export person related data to the care of other controllers. And will therefore need to keep a log or record of who was supposed to do what when..Given that people tend to sign up to SAAS nowadays.
- In other words, this is going to need to be planned as an architectural issue as opposed to "its just a delete exercise.... ".
- The same kind of complexity will occur for objections and DSAR's.
- You can take this short GDPR Quiz to find out where you stand for some of the Microsoft technical aspects of the GDPR Compliance.
- Getting started with MS GDPR
- Check what Data Centre you are using
- Investigate MS compliance toolkits
- The Microsoft Service Trust Portal (STP) provides a variety of content, tools, and other resources about Microsoft security, privacy and compliance practices. It also includes independent third-party audit reports of Microsoft's online services, and information about how our online services can help your organization maintain and track compliance with standards, laws, and regulations, such as GDPR.
- Use Compliance Manager to help meet data protection and regulatory requirements when using Microsoft cloud services
- Make sure all staff have had the right training and record this.
- All staff must be able to show written procedures for GDPR data and that they are complying with them.
- All staff must know how to handle a DSAR request
- All staff must know how to handle an actual or suspected data breach
- If data is particularly sensitive create a policy to not only lock the PC but turn the PC screen off.
- Consider a device that is part of the users access pass that they have to have with them also being necessary to unlock a PC. That way if they leave their desk it auto locks the PC.
- Make sure that ICT users of GDPR data position them selves and their desks carefully that no one can read the information from the computer/laptop/mobile screen while you’re working. Where you have a device screen on a PC/tablet or phone that might be overlooked and that could contain sensitive data consider fitting a privacy filter like those at Targus
- If your device has Trusted Platform Module (TPM) built in use it and make sure in future you buy kit with TPM.
- If you don’t have use Windows Bitlocker with USB stick for control. Always keep the emergency activation key as I have had scenarios where updating Windows 10 broke the Bitlocker USB activation and needed the Emergency key sting.
- For SME backup consider using the Diskashur 2 GDPR approved external drives.
- All electronic hardware has to have a regular process to check and update any firmware and to monitor for EOL on the device so it can be replaced as it wont be updated. Devices to check include :
- PC BIOS
- LAN controller firmware
- Disc RAID controller firmware
- Router and switch firmware – dont forget home devices and access points
- Fire and burglar alarms
- Door access control systems
- Encrypted USB sticks
- IoT devices about the home such as Hive
- Set out and record the actions taken for data wiping and disposal for all devices used in the company.
- Conducting a Privacy Impact Assessment (PIA) to be sure all CCTV cameras serve a legitimate purpose.
- Allowing CCTV systems to be on / off switchable, where appropriate, so recordings of footage are not continuous. Audio and video need to be independent (on / off) from each other as well. Legitimate reasons for recording either or both need to be clearly established.
- Sound recordings should only be obtained only where absolutely necessary to support the legitimate reasons. The use of CCTV surveillance systems should not be ‘normalised’ in the working environment to record conversations between the public and employees.
- Recordings from CCTV systems need to be securely stored and access restricted to authorised personnel.
- CCTV recordings need to be of an appropriate quality to meet the purpose intended.
- Regular checks are needed to ensure date and time stamps recorded on images is accurate.
- Recording and playback functions need to provide access to recordings made in specified locations and times to comply with subject access requests from individuals in recordings or in response to police requests.
- Appropriate policies need to be in place so that employees know how to respond to requests from individuals or police for access to CCTV recordings.
- Ensuring appropriate security safeguards are in place to prevent interception and unauthorised access, either copying recordings or viewing.
- CCTV recordings that no longer serve a purpose need to be deleted. Clear documentation of the information retention policy which is clearly understood by CCTV system operators.
- The need for signage and the availability of other appropriate information. There is a need to notify individuals of surveillance information processing, such as their presence in an area where CCTV is in operation, and their rights of access to recordings/images of themselves
- Make sure it only covers the data under that case so if you are recoding the till in a store don’t include customers if they are not in the case. If you are say a jewellery store and record the whole shop make sure you don’t cover the outside.
- Some commentators take the view that as CCTV can be recording are large number of people then the owner/operator of the CCTV are covered under “regular and systematic monitoring of data subjects on a large scale” and as such they would need a DPO. So for small organisation make sure that any CCTV you have only data on subjects of note to you – point the camera at say the inside of the door rather than the street.
- ICO has 44 page guidelines.
- Where a user works with sensitive or personal data, make sure you have a clear desk policy, which means making sure they don’t leave information which is sensitive or personal on your desk, on the printer or on the photocopier and lock papers away before leaving, storing the keys safely.
- In cases where notes are taken that include personal data consideration should be given to:
- Keeping such notes in locked briefcase when on the move
- A policy to burn / cross shred all such notebooks when done
- Where notes are then at say a phone desk then use an A4 wipe clean white board and marker.
- GDPR covers paper records as well. Make sure that in any policies you have you:
- Detail how all printouts that contain GDPR data are
- restricted to those who need them
- only kept as long as your policy states
- destroyed properly after finished
- access is controlled if they leave the office – locked briefcases
- Set out how to trawl paper records if you get a DSAR
- Ensure all staff know GDPR covers paper records and what to do if they find records outside the company policy – for example the cleaner finds names and addresses on a list when emptying a waste basket
- Detail how all printouts that contain GDPR data are
- Loss of data on paper records is a reportable incident if these are the only copies.
- Where records are kept on paper that are subject to GDPR, such as HR records, then these must have a written controlled access policy and access log. They should be kept in at least a fire proof area under lock and key in a restricted access area.
- Where written records include data in the sensitive category consider having codes to reference this data and hold the lookup codes in a separate secure store/safe.
- The GDPR only applies to loose physical business cards if you intend to file them or input the details into a computer system. It has been argued that receipt of a card direct form the person on the card is clearly consent to be contacted by not only the individual but also the company they represent to follow up the business opportunity, so placing them on a CRM is legitimate - subject to relevant retention policies etc – but only for legitimate business purpose. Some companies re putting a link or a QR code on the cards to the privacy policy attaching to the data on the card. Electronic business cards are covered by GDPR.
- If an employee (current or no longer employed) asks for their data and that data contains details of comments made identifiable mangers or others (such as a complaint) the ICO says that opinions are personal data however they are also other data subjects personal data who made the opinion. You cannot reveal that opinion without consent from the person who made that opinion to the requestor. Therefore the requestor has no right to that data unless he has consent from the person who made that opinion. Other data that includes opinion such as dating sites is still under discussion.
- Make sure you check out the GDPR position on Data Acquisition and Management specialists, including Offshoring/Outsourcing, GDPR preparation and Business Coaching before using them.
- Use of Fingerprint scanning counts as processing of Special Category data, and you require the employees consent to use this type of system.
- References you give are exempt from subject access if you give them in confidence and for the purposes of an individual’s education, training or employment or the provision of a service by them. There is no such exemption for references you receive from a third party. If you receive a SAR relating to such a reference, you must apply the usual principles about subject access to decide whether to provide some or all of the information contained in the reference. For Example if Company A gives a reference about an employee to Company B. If the employee makes a SAR to Company A, the reference does not have to be disclosed. If the employee makes the SAR to Company B, the usual SAR rules apply.
For Marketing Data Gathered Prior to May 25, 2018 you need to re-affirm consent in a GDPR compliant way where it is CURRENTLY legal to do so. The re-affirmation of consent must be done prior to 25 May 2018 and leaves you with consent that is valid to use after May. After May you can only contact people for marketing purposes (including confirming marketing preferences) from whom you have consent captured in a GDPR compliant way and can evidence it.
- With your ISP check out where their data centre and what is the standard its operating under.
- Do you have a policy in place to ensure personal data in emails is examined before sending such as Microsoft DLP, Azure IP, reverse checking the end locations of an email address (outside EU).
- Create procedures to search emails if you get a DSAR.
- Consider using encrypted email like that available in O365
- If you have the name and number of a business contact on file, or their email address identifies them (eg initials.lastname@company.com), the GDPR will apply.
- Be very careful about CC and BCC as in using these you could be giving GDPR covered emails to third parties without the original email owners consent. Use email groups and keep data on who has subscribed making sure to sent email without the CC and BCC.
- Video on data redaction for inclusion in DSAR reply
- Reviewing your whole privacy policy – a template
- Documenting your records processing some templates
- Blockchain clashed with GDPR
- DPO overview plus EU view
- Apple tools and GDPR
- GDPR training
- Rights and Scope of GDPR for non-EU Residents .Its about where you reside .
- Centralised compliance to Manage Personal and Special Category Data
- Recording processing activities