Fixed Line
Fixed line internet connection devices usually have a boundary firewall built in. Most users know firewalls protect you from the internet but they can do much more than guard basic access. They can be used to classify and control traffic like setting email send/receive at a lower priority that voice, monitor for AV/Spam and monitor intrusion detection (IDS).
If you have a fixed real world IP address many devices allow secure access using dial in Virtual Private Network (VPN) and site-to-site VPN Tunnels. Some organizations force users to connect into the company VPN to access resources, enforce corporate policies, segment networks, handle multiple internet connections and much more.
A lot of these functions are provided with the border devices listed under Wireless but in some cases extra functionality is needed for advanced protection with the likes of Watchguard and Sonicwall devices which have annual fees to keep them updated against the latest threats. You can also use cloud based scanning like OPSWAT as used by the top USA government agencies.
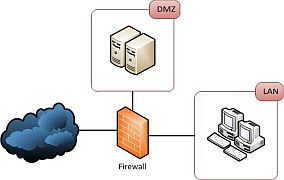
At the firewall there are also options for handling traffic to ensure it is routed to the correct LAN segment like for example a Demilitarized Zone (DMZ) for intent facing servers or a network with guest WIFI for visitors.
Once inside the network there are a vast range of network monitoring tools and switch devices to route and control traffic. Of note is the PoE switch that allows devices like cameras to be powered from the switch over the LAN cable rather than use a local mains power source.
Devices like PC’s and Mobile devices should also have a software firewall and that is often supplied as part of a paid for package like Norton on PC or LostNet on Android.