TWO FACTOR AUTHENTICATION OVERVIEW
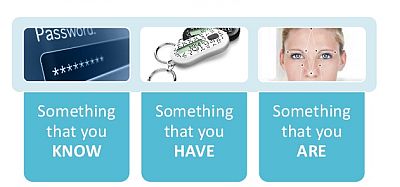
Two Factor Authentication (2FA) means that you need two pieces of information to gain access to a resource. In most cases this consists of a password plus some other identity checking method.
General Options
In practice options for 2FA after you pass password checking include:
- A text sent to a phone to enter online
- A call to landline with a code to enter online
- An application that runs on an authorised phone and sets new code every 30 seconds to enter online
- A push notification to your phone or registered device to verify on the device
- A separate dongle device with a secret string that is used with the dongle to enter online
- A dongle device with a card that inserts into the device
- RFD/NFC card reader
- Facial recognition
- Finger print or palm or ear recognition
- Heart beat recognition
- After password entered confirm a pre-selected image and string
- After password entered enter additional access and passcodes - usually you are only asked for a random few parts of these details to prohibit key-logging software from recording all your details
In theory you can use a signature looking at patterns, pressure, speed, and pen orientation but we have found that this is too variable in giving false negatives.
If for some reason you get locked out options to reset include:
- Your identity administrator
- Another email account
- A special code string
- A dongle
Micrsoft is looking past passwords to using multi factor authentication in Windows Hello for business where one part is usually the TPM chip on your PC.
Our Office 365 2FA Experience
We started using 2FA with O365 Q1 2015 but had to stop because:
- There were too may apps that did not support it or the bypass codes did not work
- Where apps did support it there were caching and single sign on issues so we had to enter a code every time an app opened
- PowerShell did not support 2FA
We restarted using it a Q2 2016 as the issues above are much reduced. The following are of note.
2FA Options
An end user can login to O365 using a browser and setup and control their 2FA options.
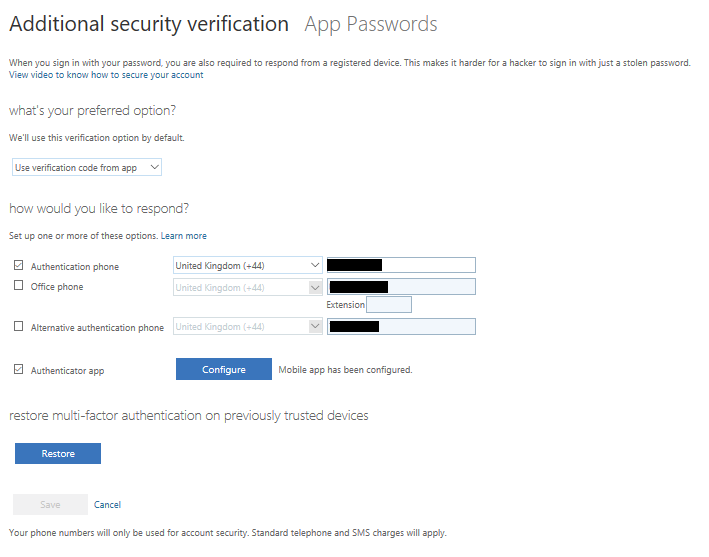
App Passwords
Many O365 apps now support app passwords. An end user can login to O365 using a browser and setup an app password to bypass 2FA for that app on that device. When you generate an app password give it a meaningful name and keep a copy as you cannot access it again once the first view is closed. When the app is launched you only need to use the main password and sometimes not even then if Single Sign On works with that app. If for some reason the device is compromised then a user can logon to O365 in a browser and remove the special password for the client on thet device and stop just that app on that device from working.
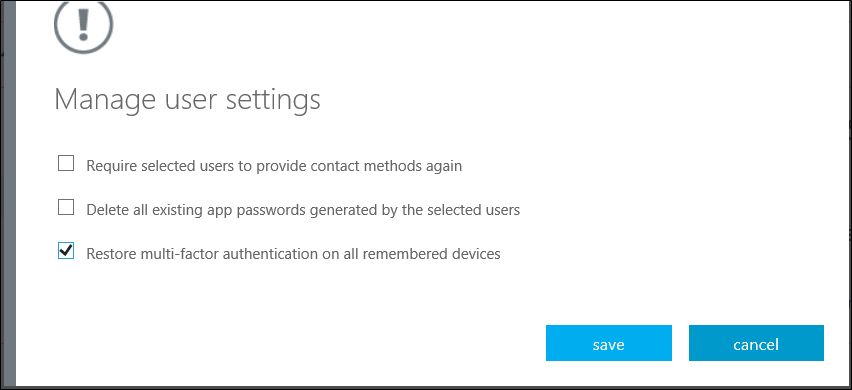
Administrators cannot change these app passwords but they can:
- Require users to provide contact methods again
- Delete app passwords
- Require MFA on all trusted devices
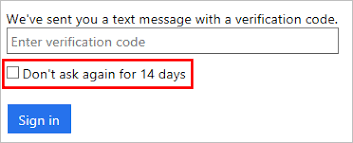
On most devices that use 2FA you can now select a box to not be asked for the code again for 14 days.
Related
- Setting up 2FA for Office365 user
- Setting up 2FA for Office 365 admins
- Checking if a site you use supports 2FA